CATEGORY
Physical Security Services
Physical security service is defined as the protection of any facility, using security guards and electronic security systems.
Beroe LiVE.Ai™
AI-powered self-service platform for all your sourcing decision needs across 1,200+ categories like Physical Security Services.
Market Data, Sourcing & Supplier Intelligence, and Price & Cost Benchmarking.
Schedule a DemoCategory Alerts
CCTV systems to be debarred from procurement
March 09, 2023ALLIED UNIVERSAL?S STRATEGIC MOVE ON FILLING THE EMPLOYEE SHORTAGE GAP
October 31, 2022Acquisition Game still ON- Allied Universal expanding in the universe of security solutions
September 12, 2022Become a Beroe LiVE.Ai™ Subscriber to receive proactive alerts on Physical Security Services
Schedule a DemoPhysical Security Services Industry Benchmarks
Savings Achieved
(in %)
The average annual savings achieved in Physical Security Services category is 9.00%
Payment Terms
(in days)
The industry average payment terms in Physical Security Services category for the current quarter is 45.0 days
Compare your category performance against peers and industry benchmarks across 20+ parameters on Beroe LiVE.Ai™
Category Strategy and Flexibility
Engagement Model
Supply Assurance
Sourcing Process
Supplier Type
Pricing Model
Contract Length
SLAs/KPIs
Lead Time
Supplier Diversity
Targeted Savings
Risk Mitigation
Financial Risk
Sanctions
AMEs
Geopolitical Risk
Cost Optimization
Price per Unit Competitiveness
Specification Leanness
Minimum Order Quality
Payment Terms
Inventory Control
The World’s first Digital Market Analyst
Abi, the AI-powered digital assistant brings together data, insights, and intelligence for faster answers to sourcing questions
Abi is now supercharged with GPT4 AI engine. Enjoy the ease of ChatGPT, now on Abi
Physical Security Services Suppliers
Find the right-fit physical security services supplier for your specific business needs and filter by location, industry, category, revenue, certifications, and more on Beroe LiVE.Ai™.
Schedule a Demo


Use the Physical Security Services market, supplier and price information for category strategy creation and Quaterly Business Reviews (QRBs)
Schedule a DemoPhysical Security Services market report transcript
Global Security Services Industry Outlook
-
In 2022, the global security service industry was valued at approximately $412 billion. By the end of 2026, it is expected to reach $425.6 billion with a Compound Annual Growth Rate (CAGR) of 12 percent, which is expected to decrease due to COVID-19 impact, where surveillance spend is cut across major industries due to halt in business
-
The increase in crime rates, social unrest within countries, and terrorism have fuelled the demand for better security solutions all over the globe
-
Security equipment used by guards has also undergone developments, such as vapor tracer, which enables detection and identification of all types of vapors and traces of organic, biological, and chemical compounds correctly and in brief time
-
Advancements have also been made in existing products, such as CCTV, access control, etc., where the products are getting equipped with features, such as 360-degree view CCTV, Bluetooth Enabled Access Control, etc. These technological advancements in the physical security market are expected to drive the growth of the market in the coming years.
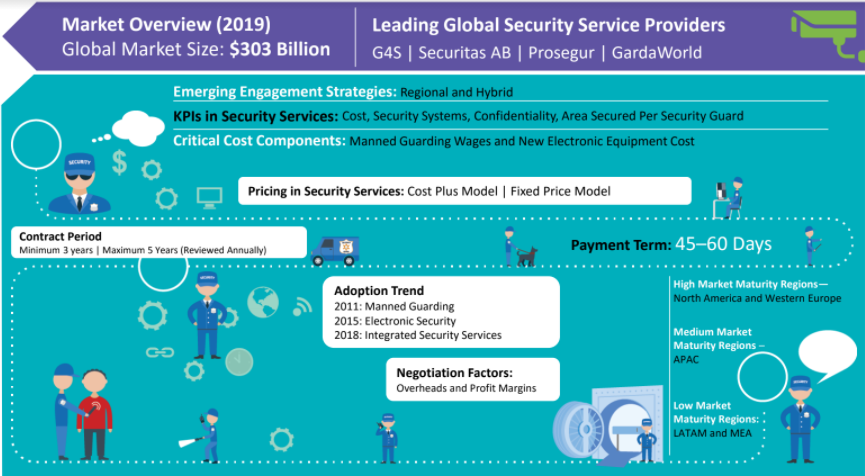
Global Security Services Market Maturity
-
The rising social insecurity in the recent times is prompting the buyers to be more proactive in securing their premises
-
Technology plays a huge role in reducing the labor required. Increasing the investments in unmanned guarding will reduce the cost of services as it is directly related to the labor cost
-
The adoption of technology which requires high capital investment is limited to the mature markets and is making slow inroads in the developing regions
Global Security Services Drivers and Constraints
-
Technology is a double-edged sword. On one hand, the adoption of new technologies (such as CCTV and electronic surveillance systems) reduces cost, and on the other, there is a threat to data security, which causes a rise in demand for it
-
Cost savings from 20–80 percent can be achieved in the long run depending upon the buyer’s area under surveillance and rate of adoption of unmanned guarding. The cost savings would increase over successive years as the total cost of ownership (TCO) for electronic equipment gets written off every year
Drivers
-
The increasing demand for security services in different segments and the arrival of new entrants has lead to more competition among service providers and higher fragmentation in the U.S. and Europe.
-
The increasing threats of social insecurity, terrorism and rising crime rates raises the concern for securing assets, employees and information; hence, the security services industry will have a potential growth period.
-
The increase in infrastructure, such as malls and office complexes, will in turn require more manpower; hence, the security service suppliers will have a potential growth period in their businesses.
Constraints
-
The lack of common procedures and standards across borders has resulted in operational problems for security devices in different regions. This restricts buyers from investing in technology and security equipment on a large scale.
-
Lack of awareness of new technologies and security devices among buyers might result in slower adoption of electronic security services, especially in emerging regions.
-
The availability of a skilled labor force in emerging regions is quite low as compared to mature markets like Europe and the U.S. This results in increased labor shortage, training costs and reduced quality of services.
-
As the pandemic unfolded, production of semiconductor chip fell behind, resulting in a lack of semiconductors needed to guide smart products. This has also impacted businesses in need of advanced security products and services.
Key Industry Trends : Global Security Services
Security as a Service:
-
Physical security services are moving towards a system that provides more specific solutions as well as a higher level of integration and service. Instead of viewing physical security as a series of connected hardware and software systems, the industry has started to move towards system that provides more of security as a service to successfully run security operations.
Deeper Convergence of Physical and Logical Security:
-
The upcoming convergence of physical and logical security is an absolute certainty, which is already in progress. For example, Role-Based Access Control (RBAC) has been the predominant model for access control in the IT world of logical security and today this architecture is reflected in the design of leading access control systems, because it significantly reduces the cost of access management.
Shift from Proprietary to Open Hardware:
-
Security dealers and integrators have started to manufacture hardware that are compatible with third party operable software. This is mainly because of the issues customers faced in the past due to the manufacturer’s negligence in updating the software or discontinued operations. The customers feel guaranteed with the invention of these open hardware which can also be run on other third-party operating software (apart from OEM).
More Focus on Video Analytics:
-
The security industry has started to develop video analytics software that works in a similar way to software that analyzes numerical and text data. Instead of having a person to work through video footage, the software can work in real time to help make quick and informed decisions. This would help professionals address several challenges such as facial recognition, forensic analysis and perimeter protection.
Integrated Cloud Systems:
-
Integration of various security systems in an organization have been the trend for quite some time and now the cloud storage is being utilized to achieve maximum operational efficiency through integration. This not only integrates the security systems in an organization, but also provides the user a remote access to the security network, which could be used in techniques such as intrusion prevention which is different from intrusion detection.
Why You Should Buy This Report
- The report gives information on the regional and global physical security market size, maturity, industry trends, drivers and constraints.
- It gives a regional market outlook of the physical security equipment market in the APAC, North America, MEA and Europe regions and Porter’s five force analysis of the developed and emerging markets.
- It provides insight into the supply landscape of the global physical security equipment market and does a SWOT analysis of key players like GardaWorld, Prosegur, Brink’s, etc.
- The report details the cost breakup, cost analysis, pricing analysis, pricing models, etc. of physical security services.
Interesting Reads:
Discover the world of market intelligence and how it can elevate your business strategies.
Learn more about how market intelligence can enable informed decision-making, help identify growth opportunities, manage risks, and shape your business's strategic direction.
Get Ahead with AI-Enabled Market Insights Schedule a Demo Now
