CATEGORY
Manned Guarding Services in Australia
Manned guarding service is the deployement of security guards to protect any facility
Beroe LiVE.Ai™
AI-powered self-service platform for all your sourcing decision needs across 1,200+ categories like Manned Guarding Services in Australia.
Market Data, Sourcing & Supplier Intelligence, and Price & Cost Benchmarking.
Schedule a DemoThe World’s first Digital Market Analyst
Abi, the AI-powered digital assistant brings together data, insights, and intelligence for faster answers to sourcing questions
Abi is now supercharged with GPT4 AI engine. Enjoy the ease of ChatGPT, now on Abi
Manned Guarding Services in Australia Suppliers
Find the right-fit manned guarding services in australia supplier for your specific business needs and filter by location, industry, category, revenue, certifications, and more on Beroe LiVE.Ai™.
Schedule a Demo


Use the Manned Guarding Services in Australia market, supplier and price information for category strategy creation and Quaterly Business Reviews (QRBs)
Schedule a DemoManned Guarding Services in Australia market report transcript
Regional Market Outlook on Manned Guarding Services in Australia
Buyers can look at bundled services to reduce costs, as FM companies are increasingly offering security as a bundled service by combining it with other services.The Security Services industry in Australia has recorded a revenue of approximately AUD 6.2 billion in 2016. It has grown at a rate of 1.3 percent annually from 2012 through to 2018.
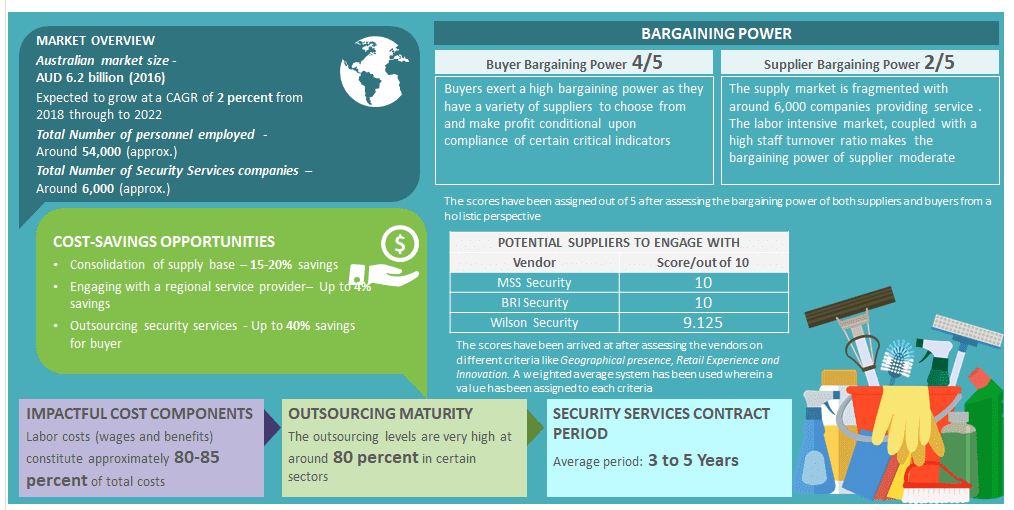
- The security industry in Australia employs more than 54,000 security personnel nationally
- There are more than 6,000 active security service companies in Australia
- The security service industry is a highly competitive market with profit margins ranging between 8-12 percent
- There has been a trend of supplier consolidation in the Australian market over the past decades
- The security services market in Australia is primarily concentrated to Sydney, Melbourne and Brisbane
Key Industry Trends
Security as a Service:
Physical security services are moving towards a system that provides more specific solutions as well as a higher level of integration and service. Instead of viewing physical security as a series of connected hardware and software systems, the industry has started to move towards system that provides more of security as a service to successfully run security operations.
Deeper Convergence of Physical and Logical Security:
The upcoming convergence of physical and logical security is an absolute certainty, which is already in progress. For example, Role-Based Access Control (RBAC) has been the predominant model for access control in the IT world of logical security and today this architecture is reflected in the design of leading access control systems, because it significantly reduces the cost of access management
Shift from Proprietary to Open Hardware:
Security dealers and integrators have started to manufacture hardware that are compatible with third party operable software. This is mainly because of the issues customers had faced in the past, due to the manufacturer's negligence in updating the software or discontinued operations. Customers feel guaranteed with the invention of these open hardware, which can also be run on other third party operating software (apart from OEM).
More Focus on Video Analytics:
The security industry has started to develop video analytics software that works in a similar way to software that analyzes numerical and text data. Instead of having a person work through video footage, the software can work in real time to help make quick and informed decisions. This would help professionals address several challenges such as facial recognition, forensic analysis and perimeter protection.
Integrated Cloud Systems:
Integration of various security systems in an organization have been the trend for quite some time and now the cloud storage is being utilized to achieve maximum operational efficiency through integration. This not only integrates the security systems in an organization, but also provides the user a remote access to the security network, which could be used in techniques such as intrusion prevention which is different from intrusion detection.
Industry Drivers and Constraints
- Technology is a two edged sword, on one hand adoption of new technologies (such as CCTV and electronic surveillance system) reduces cost and on the other there is a threat for data security, which causes a rise in demand for it
- Technological advancement has been driving the industry, as well as has developed an urge for progress of cyber security tools to protect cloud storage and data privacy
Drivers
- The increasing demand for security services in different segments and the arrival of new entrants has led to more competition among service providers and higher fragmentation
- Increasing threat of cyber security, as well as terrorism, has influenced organizations to advance safety values, thus promoting industry growth
- Factors such as growing expenditure on the security of critical infrastructures, rising adoption of cloud–based data storages and data analytics employed by organizations are fueling the market
Constraints
- Lack of awareness about new technologies and security devices among buyers might result in slower adoption of electronic security services, especially in emerging regions
- Unlike Europe and the US, availability of skilled labor in Australia is quite low for security services. This results in increased training costs and reduced quality of services
- Absence of correlation among security solutions and privacy concerns against the installation of surveillance cameras are hindering market growth
Interesting Reads:
Discover the world of market intelligence and how it can elevate your business strategies.
Learn more about how market intelligence can enable informed decision-making, help identify growth opportunities, manage risks, and shape your business's strategic direction.
Get Ahead with AI-Enabled Market Insights Schedule a Demo Now
