Incident response plan helps to reduce data breach costs

Abstract
For global organizations, preparing for a data breach can be a complex process. A breach may involve theft of identity, credit, data, health information, personal information and more. Once a data breach occurs, organizations typically implement an incident response plan, which includes discovery, notification, and remediation. Though internal stakeholders such as legal, privacy, PR, and others have a role in the response plan, external experts play a major role in providing guidance that help organizations respond quickly to notify affected individuals. In general, 60-70 percent of the organizations have a data breach response plan.
This article will cover the following aspects on the rising threat of data breach:
- How implementing a response plan drives down the cost of a data breach?
- Incident response plan structure
- Key technology trends
- Impact of a incident response plan
Introduction
Data breach and identity theft have now become industries of their own due to the alarming frequency of high profile breaches and growing cost to organizations worldwide. An incident response plan specifically addressed those measures to be taken in the event of a breach thereby including the responsibilities of the response team.
Response plan and cost of a data breach
Every company should be focused on preventing, detecting and having the right capabilities to respond to data security incidents. The average cost of data breach is expected to increase from $3.79 million in 2016 to $4 million in 2017. Having an incident response plan in place has become a critical component for every industry.
Programs that preserve customer trust and loyalty in advance of a breach will help in reducing business loss. Having a breach response plan in place can reduce the cost by nearly $40,000. Having access to an internal or external incident response team will reduce the cost to a greater extent.
When there is a breach, the incident response team typically accelerates the time frame in which security events are contained, preventing further loss of data. This plays a significant role in reducing the overall cost of a breach.
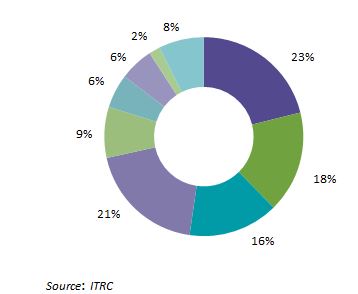
Highly regulated industries such as healthcare, education and financial services substantially have a higher data breach cost. Consecutively second time in a year, healthcare represented the highest percentage of breach incidents at 23 percent. Healthcare industry possesses valuable data such as medical records, billing and insurance records, and payment details which have more demand in the market. Data breach in healthcare industry is currently costing $6.2 billion.
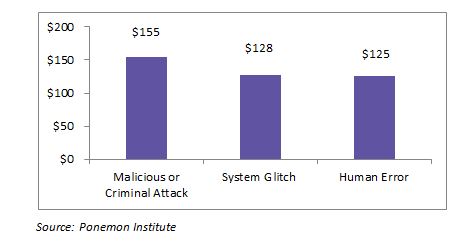
Malicious and criminal attacks cause most data breaches. In 2016, the costs of breaches due to these attacks were around $150 (per capita cost).
Creating an incident response plan
The most effective way to develop a data breach response plan is to retain the service of a data breach resolution partner. Many companies provide end-to-end services ranging from pre-breach response to call center support. Ahead of an incident, an external partner needs to have an incident response plan which follows best practices and latest developments in the threat landscape.
- Alert and Activate the response team which includes internal incident lead, FBI, Forensics and external vendor
- Secure the area of operation where the incident occurred as it helps to preserve the evidence
- Prevent additional data loss by taking affected systems offline until the forensics team arrives
- Incident Assessment – Assess priorities and risk based on the breach. Asses the type of breach, for example: Insiders, illegal access
- Contact External resolution partner – Contact pre-selected vendor to choose business services for the firm and protection products for individuals affected in the breach. External partner supports in notifying the customers, stakeholders through emails, calls and letters
- Review Protocols regarding publishing information about the incident. Restrict information until there is a communication plan in place and legal counsel is involved
- Review Cyber Insurance Coverage to ensure the premiums and approval amount based on parameters such as data risks and exposure are all worked out
- Notification – Restrict information until there is a notification plan. Supplier should assign an experienced account manager to help streamline and simplify the notification process
Technology trends
Encryption refers to algorithmic schemes that encode plain text into a non-readable form called cipher text, thus providing privacy for the encrypted data. End-to-end encryption ensures that the transaction is never transmitted in plain text in the frame relay, dial-up or internet connection, where the potential exists for interception by fraudsters. This is the only technology when it comes to protecting sensitive data residing within the cloud and IoT. 60 percent of the global organizations encrypt data in the public cloud and 40 percent in IoT. Cloud services have an extremely high level of security; it is encrypted and monitored by a team of experts who identify malicious traffic.
MFA-Multi factor authentication is a security system which requires authentication at various levels from independent categories of credentials to verify user’s identity for login or transaction. In retail and e-commerce ecosystem, implementing MFA for transactions tied to existing web analytics can increase assurance in purchaser and protect user identity. This helps to reduce the risk of false online identification and authentication fraud.
Intrusion detection systems (IDS) and intrusion prevention systems (IPS) constantly monitor the network, identify possible incidents and stop them, check logging information and report it to security administrators. IDS and IPS have become a necessary addition to the security infrastructure of all the Industries because they can stop attackers from gathering information about the network.
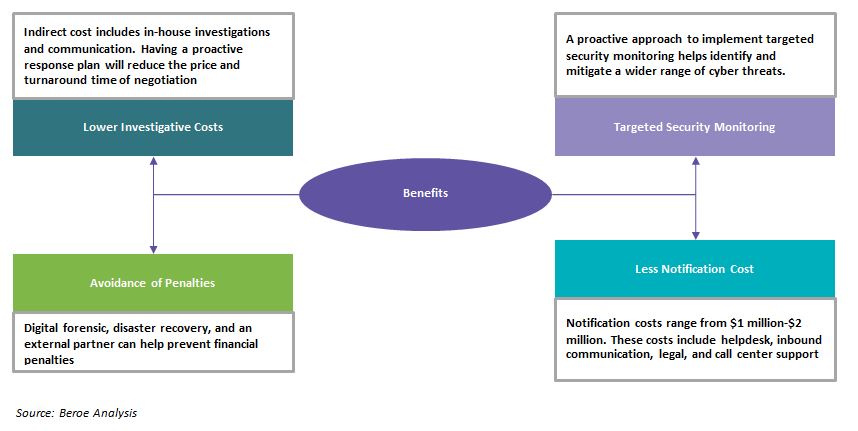
Benefits of incident response plan
Conclusion
Data breach has been increasing year-on-year. The foremost step of planning includes bringing in a trusted outside partner to investigate the incident to determine the intensity and the after effects of the breach. Part of this planning includes identifying when to bring in a trusted outside partner to investigate an incident and determining the type of incidents to investigate.
When it comes to data breach response services, there are a handful of firms that can provide end-to-end services. The incident response rate can be greatly increased when the buyer engages with a service provider prior to a breach and uses their expertise in controlling the incident. Having an incident response team in place will also help to reduce the cost to a greater extent.
Breach response plan needs to have processes that are regularly updated as the threats faced by the organizations will continue to evolve.
Related Insights:
View All
Get more stories like this
Subscirbe for more news,updates and insights from Beroe