
Cybersecurity and Procurement: suppliers are key partners

Praveen Dahiya, Associate Vice President and Anand Vaidyanathan, Lead Analyst

Within most companies, procurement is one of the functional domains most vulnerable to cyber-crime. According to a recent Global Economic Crime Survey 2016 conducted by PwC, procurement fraud is the fourth most commonly reported economic crime.
Furthermore, in most cases, fraud is detected during audit, after the losses have occurred. Large companies with 1000 or more employees are relatively more susceptible to procurement fraud, according to PwC report.
The year 2020 will probably see more than 50 billion interconnected devices globally. And Internet of Things (IoT) will begin to exert its impact on all businesses across the globe, including the procurement vertical. However, with increasing usage of devices that have inbuilt sensors, processors or internet connectivity, there is also the specter of hackers trying to disrupt the procurement processes.
Weaving Cybersecurity clauses into the contracts
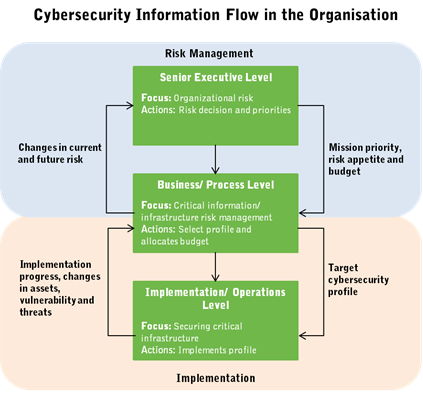
Procurement teams often share sensitive information such as product blueprints, intellectual property and other confidential information with suppliers for better collaboration.
It is essential for category managers to protect vital information from being leaked out or hacked. Contracts should have clauses that address the following:
- Suppliers do not voluntarily share buyer's confidential information to anyone outside the intended group
- Supplier takes necessary cybersecurity measures to prevent leak of information in case of a cyber-attack
Evaluation of supplier’s cybersecurity infrastructure
Suppliers can either opt for self-assessment or get their systems accredited by a third-party testing body. However, most of the standards require third-party testing.
In order to ensure suppliers have robust security systems, sourcing managers can:
- Mandate the suppliers to conform to an existing industry standard
- Device a custom standard and ensure supplier compliance through self-assessment or third-party accreditation
Cybersecurity evaluation
Cybersecurity evaluation process usually involves the following:
- A questionnaire for understanding the nature of supplier's information systems
- Testing of various components of the system such as network, host, servers etc., in order to check the efficacy of cybersecurity programs
- Evaluating compliance with existing cybersecurity standards based on test results and supplier's information security policy
In many organizations, procurement is entrusted with selecting cybersecurity vendors. Depending on the business need, there are several contracting models that sourcing managers can make use of.
Contract Models
-
Cost effective integration
The critical cyber security infrastructure should be procured from preferred or best vendors who are into IT Services and Software. Design of security infrastructure, building of security system and administering the entire system should be outsourced to the same supplier for cost effectiveness.
-
End-result contracting
The end-result contracting provides for higher efficiency and cost savings from the vendor. This is suitable when the companies look for Cyber Security Software.
-
Multi-year agreement
If the procurement teams are satisfied with the quality of service currently provided, additional cost savings can be achieved through the purchase of a multi-year agreement. This is applicable when the company looks to upgrade its cyber-security software infrastructure.
-
Service contract
Purchasing a service contract ensures that preventive maintenance will be performed at regular intervals, thereby eliminating the possibility of unexpected maintenance costs. This will help companies to periodically assess their IT systems and go for an upgrade, if required.
Identification of best-fit service providers
Cyber security suppliers can be segmented under following categories:
- Software and IT services
- Advisory and Auditing
- Software Security
- Business consulting
Based on the business requirement, procurement teams need to develop appropriate models to identify the most suitable suppliers
| S.No |
Business Need |
Suitable Supplier |
Contracting Model |
|
1 |
Cyber Security setup with full support |
IT Services and Software |
Cost Effective Integration; Purchasing a service contract |
|
2 |
Penetration Testing and Vulnerability Assessment |
Advisory Companies |
End Result Contracting |
|
3 |
Upgrading Cyber-security Software system |
Software Security company |
Multi-year agreement |
|
4 |
Upgrading Cyber Security Infrastructure |
IT Services and Software |
End Result Contracting |
Related Insights:
View All
Get more stories like this
Subscirbe for more news,updates and insights from Beroe







